Keylogger for Social Media: Pros & Cons Revealed
A survey found that 79% of Americans are worried about how businesses handle their personal data, with 84% expressing concerns over online privacy and security.
This reflects a growing distrust in how companies manage consumer information, especially with social media and targeted ads.
We will take a look at the controversial world of keyloggers for social media.
This topic is hotter than ever, with privacy concerns skyrocketing and tech evolving at breakneck speed.
Let's peel back the layers and explore the good, the bad, and the downright shocking aspects of using keyloggers in the social media sphere.
By the end of this article, you'll be an expert on this digital spy tool.
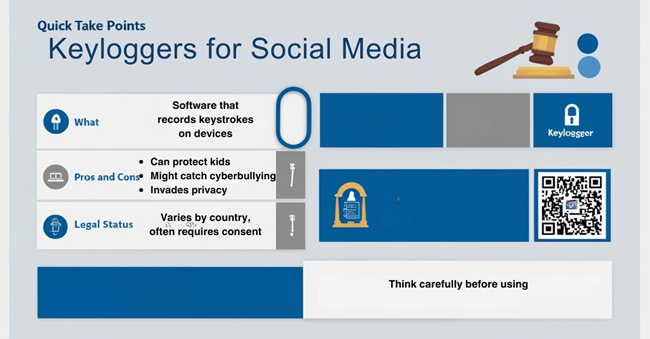
📌 Keylogger for Social Media: Quick Take
- What: Software that records keystrokes on devices
- Used for: Monitoring social media activity
- Pros:
Can help protect kids online
Might catch cyberbullying
Could recover lost data
- Cons:
Invades privacy
Often illegal without consent
Can damage trust in relationships
- Legal status: Varies by country, often requires consent
- Ethical concerns: Balances safety vs. privacy
- Protection tips:
Use strong passwords
Keep software updated
Be cautious online
Use good antivirus software
Think carefully before using – risks often outweigh the benefits.
What Exactly is a Keylogger for Social Media?

Okay, imagine this: It is 2 in the morning and there I am with my computer trying to reset my social media password. In my desperation, I found something called a “keylogger,” which I had to think about.
I didn't realize I was just on the verge of opening a can of worms that would change how I viewed online privacy forever.
What, in the name of heavens, is a keylogger?
To put it simply, it is software that monitors and records every keystroke of your keyboard.
Oh yeah?
Every single key that you press on your phone – tablet or gadget is also recorded. From your passwords to your private messages, nothing escapes its watchful eye.
In the case of social media, hardly will you be able to write a single word on Facebook, Instagram, or Twitter without these programs recording it.
Now, there are two main types of keyloggers: hardware and software.
Hardware keyloggers
There are hardware keyloggers that come as portable devices that one inserts into the computer. They're like those fake rocks people use to hide house keys, except instead of hiding keys, they're hiding… well, your keys (the ones you type, that is).
Instead of fake rocks hiding the keys these devices hide typing keys (“the keys pressed in keyboards”).
Software Keyloggers
Software keyloggers' are programs that run in the background of your device, silently doing their thing without you even knowing.
But this is where it gets more fun. The progress of keyloggers is even faster than that of Pokemon in the age of social media.
They've gone from simple keystroke recorders to sophisticated tools that can take screenshots, track mouse movements, and even access your webcam.
I realized how powerful these tools had become when I was helping a friend recover some lost data, and we used a keylogger as a last resort.
A friend of mine had lost some data and I came to his aid. As the final solution, we decided to install a keylogger. We not only managed to retrieve the missing data but also recorded almost a week of her internet usage accidentally.
It was pretty much like looking into someone's diary without their permission – exciting, yet extremely disturbing.
The other thing is that keyloggers for social media aren't just about capturing passwords anymore.
They can track your entire online social life – your conversations, your likes, your shares, even those embarrassing late-night posts you make and delete right away (pro tip: they're never really gone).
But before you start wrapping your devices in tinfoil, let's take a deep breath and look at both sides of this digital coin.
Because like most things in life, keyloggers aren't inherently good or bad – it's all about how they're used. They can be used in some interesting ways.
The Tempting Pros of Social Media Keyloggers
Okay, I know what you are thinking. “Pros?
How can there possibly be any pros to this digital snooping?”
Well, I suggest you brace yourselves as you may be shocked.
Keeping Kids Safe Online
At a particular time, I was a fresh-faced teacher, trying to navigate the treacherous waters of keeping kids safe online. It was like trying to herd cats – digital, sneaky, always-one-step-ahead-of-you cats. That was when I first heard of the possibility of keyloggers for parental control.
I will not say that it is the best solution, but for parents who are at their wits' end trying to protect their kids from the dark corners of the internet, keyloggers can be a lifeline.
They can help parents keep tabs on their children's social media activity, potentially catching signs of cyberbullying or predatory behavior before it's too late.
There was one case where a student's parents discovered their child was being groomed by an online predator, all thanks to a keylogger. It was a wake-up call for all of us about the very real dangers lurking in the digital world.
But it's not just about child safety. In the workplace, keyloggers have found a niche in productivity monitoring.
Now, before you start having visions of Big Brother, hear me out. In some industries, especially those dealing with sensitive information, monitoring employee activity can be important for security and efficiency.
I once worked as a consultant for a company whose business strategy included the deployment of keyloggers for protection purposes.
At first, employees were very mad about that. However, with the passage of time, they understood that it also helped them in defending themselves against undue accusations and in streamlining their workflows.
It was like a digital alibi for their work patterns and habits.
Data Recovery
Here's another good surprise: data that can be restored.
Have any of you had that heart-stopping moment when you accidentally close a browser tab with an unsaved masterpiece of a social media post?
Yeah, me too. Far more often than I'd like to admit.
Keyloggers can sometimes be a saving grace in these situations, preserving your digital breadcrumbs so you can piece together your lost work.
Investigating Dishonesty in a Relationship
And of course, it could lead to investigations of possible infidelity in relationships.
First of all, let me tell you that I am not advocating so much for spying on your partner. That's a whole can of worms you don't want to open.
Nevertheless, I've seen cases where keyloggers have exposed cheating spouses or dishonest business partners, bringing painful truths to light that might have otherwise remained hidden.
Detecting and Preventing Cyberbullying
Finally, and this is a REALLY big one, keyloggers can help in the prevention and tackling of cyberbullying.
As someone who's dealt with the aftermath of cyberbullying in schools, I can't stress enough how important early detection can be. Keyloggers can provide concrete evidence of bullying behavior, making it easier for authorities to intervene and put a stop to it.
But before you rush off to install a keylogger on every device you own, calm down. Because as with any powerful tool, there's a dark side to consider. And believe me, it's more sinister than you would ever imagine…
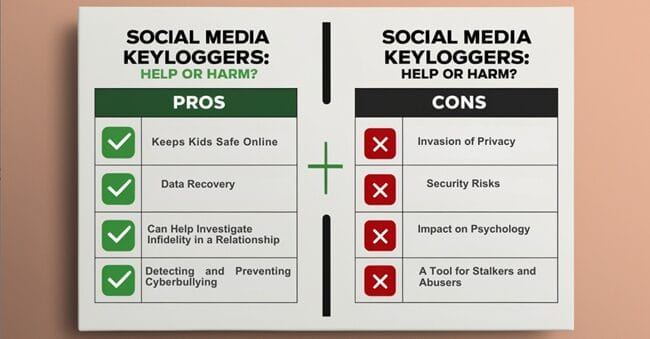
The Alarming Cons: Why You Should Think Twice
Alright, everyone, time to be serious for a minute. It's because, even though keyloggers might seem like a magic solution to all your digital worries, they come with a boatload of problems that'll make your head spin faster than a cat chasing a laser pointer.ca
Let me tell you a story. There was once a time I was performing a security test whereupon I forgot to disable the keylogger on my computer. Personal data as it were.
It was like having a nosy roommate who never sleeps, eats, or leaves the house. Every single byte of detail about a person was captured and stored. Every single password, every private message, every dumb character – were all there on screen devoid of any emotion.
I was furious, fuming even more than when someone else violated my privacy- I violated my own privacy!
Invasion of Privacy
And this brings us to the biggest, baddest con of them all: invasion of privacy.
To use a keylogger is very much like reading another person's diary, eavesdropping on their every conversation listening to their phone calls, and monitoring their movements no matter the time of the day or the day of the week.
It's a massive breach of trust that can destroy relationships faster than you can say “I can explain!”
Now let's not even go to the legal aspects.
And it is reasonable to assume that in many regions, using keyloggers without consent is illegal. I've seen people end up in hot water with the law, facing fines and even jail time, all because they thought a little digital snooping couldn't hurt.
Spoiler alert: it can hurt a lot.
Security Risk
Keyloggers, by themselves, can pose a big threat as well. It's like locking your front door but leaving a spare key under the mat with a big neon sign saying “SPARE KEY HERE!”.
To put it in simple words, a keylogger can be used by any hacker worth their salt to exploit or gain access to and collect all the juicy data and sensitive information.
And so in trying to protect yourself, you could actually be rolling out the welcoming carpet for the cybercriminals.
Impact on Psychology

And we also can't ignore the psychological aspect.
In the past, I had a student who discovered that the parents had installed a key logger so that they could keep tabs on her.
The trust that was destroyed from that?
Let's just say that even with all the family therapy sessions in the world, there was no way to fully repair that damage.
A Tool for Stalkers and Abusers
Last but not least, stalkers and abusive partners are known to use keyloggers.
I have witnessed such instances where these tools were used to control and intimidate victims, tracking their every online move.
It's a chilling reminder of how technology designed to protect can be weaponized by those with malicious intent.
So, before you even think about the keylogger solution… ask yourself: Is it worth it?
Is it worth losing trust, breaking the law, or willfully becoming a target?
Because if you do, everything changes and there is no going back. Period.
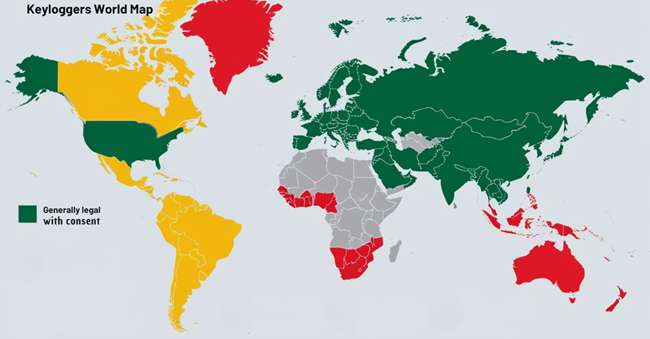
The Legal Labyrinth: Is It Even Allowed?

Okay everybody, as of now it's the time for all of you to put on your legal caps as we are now going to delve deeper into the complex issues of keylogger law.
And, in this regard, they are as clear and transparent as a politician's election promise.
One of the earliest attempts that I ever made to make sense of the law concerning keyloggers is one of the moments I still feel awkward about. It was like trying to read something written in Sanskrit while riding a rollercoaster, with a blindfold over my head.
It's that complicated.
Now here's the catch: The legality of keyloggers varies wildly depending on where you are in the world. In some of these countries, they're about as welcome as a porcupine at a balloon party. In others, they're tolerated under certain conditions.
Let's start with the United States since that's where I cut my teeth in the IT world.
Wiretapping laws and electronic surveillance laws are practices generally classified under the United States Constitution.
The general rule of thumb?
If you don't have consent, you're probably breaking the law.
There was a company that thought it would be a great idea to secretly install keyloggers on all employee computers.
It wasn't.
They found themselves in a situation where they had been sued by former employees triggering class actions, hastening the lawyers' old age by a decade in six months.
Now, when it's time to discuss issues of consent, the situation gets a bit tricky.
In some states, there is a requirement for the consent of all persons in the monitoring (called, ‘two-party consent‘ states). In other states, for example, only one person's consent is required (that is, ‘one-party consent‘ for you).
As for the workplace?
That is a totally different ball game altogether.
In most cases, the employers have a little more flexibility when it comes to the monitoring of devices that are owned by the company.
But still, these employers are, in most cases, required to inform those employees that they are under monitoring.
I've had experiences where companies have tried to sneak monitoring policies into the fine print of employment contracts.
Pro tip: Don't do that.
In the European Union, the General Data Protection Regulation (GDPR) has thrown another spanner in the works.
Under GDPR, individuals have a right to privacy in their personal communications.
Keylogging with no consent?
That's a big no-no that can result in hefty fines.
Also, don't forget the potential criminal implications.
For example, using a keylogger in order to log into someone's account or to obtain their information?
Doing any of those things is committing ‘computer fraud‘ and will get you in hot water.
Who wants that?
I once knew a guy who thought it would be a great idea to use a keylogger to get his ex-girlfriend's new Facebook password In the end, it resulted in criminal convictions and a very expensive lesson in privacy laws.
The bottom line?
If you're thinking about using a keylogger, consult with a legal professional first. And, maybe, think twice or thrice. Because navigating these legal waters is about as easy as trying to nail jelly to a wall.
Bear in mind that just because you can do something, doesn't mean you should. And when it comes to keyloggers, the legal consequences of getting it wrong can be severe.
So be careful, my friends.
Ethical Dilemmas: The Gray Areas of Digital Monitoring
Okay, guys, it's time to put on our philosopher hats, looking within ourselves and wading through ethics.
Because when it comes to looking at keyloggers and monitoring social media, what we're handling is more than pure ones and zeros. We're dealing with the trust and privacy of the society when it comes to the digital world.
The first time I really grappled with the ethics of digital monitoring was when I was an IT consultant working for a school district. We were discussing implementing monitoring software on student laptops.
On one hand, we wanted to protect children from cyber predators, or, at least, cyberbullying. On the other hand, it felt like we were practically spying on them.
Now that sure was a rock and a hard place for one to be stuck in.
The thing is, when it comes to keyloggers and social media monitoring there is a thin line drawn between safety and privacy.
It's like trying to find the perfect balance between helicopter parenting and free-range parenting, but in the digital world.
Consider parental control.
For example, we all agree that keeping our children safe and preventing them from being exploited online is the ultimate goal.
But at what point, really, does monitoring cross the line into an invasion of privacy?
I have witnessed split families where children get betrayed by excessive monitoring as parents feel guilty concerning them.
It's very unfortunate, I must say.
How about the workplace?
Well, now that's a different kettle of fish.
I used to deal with a business that adopted very extreme monitoring methods. They reasoned that it would boost productivity. Performance was dropped and morale tanked even quicker than you can say “Big Brother is watching.”
Employees felt like they couldn't even breathe without it being logged somewhere.
Well, here's the twist – there are instances where monitoring enhances trust.
I know it sounds counterintuitive, right?
But I've seen cases where transparent monitoring practices have led to increased accountability and better communication.
The key word here is “transparent.”
Sneaky monitoring?
That's a one-way ticket to ‘Distrustville', population: Your entire team.
The Role of Consent

Now, let's briefly discuss the issue of consent in all this. In a perfect world, we would always get clear, informed consent before any kind of monitoring.
But of course, we don't always live in a perfect world, do we?
In other instances, such as those where cyberbullying or other criminal acts may be taking place, waiting for an agreement or consent may lead to the loss of important evidence.
Let me give an example. There was a time when a school decided to monitor student emails, and did so even in the absence of affirmative consent. This case led to the discovery of a standout student with mental issues who had suicidal thoughts.
It was a simple ethical issue.
Is it acceptable to infringe on someone's privacy to save a life?
Alternatives to Keyloggers
Let us also consider the alternatives.
Because let's face it, there are not only keyloggers to use when it comes to digital monitoring. There are other strategies that are not as intrusive. These include content filters, activity logs, and plain talking.
As a social worker before, I came across a family who was struggling with trust issues around their teenager's internet use. Instead of resorting to secret monitoring, they sat down and had an open, honest conversation about online safety.
They established some rules together with everyone participating and agreeing on some basic monitoring tools.
Was it perfect?
No.
Yet it was still a whole lot better than sneaking around with keyloggers.
In the end, every individual, and society for that matter has unique challenges and unfortunately, there are no universal solutions to the ethical problems encountered.
It's all about weighing the pros and cons, considering the potential consequences, and making the best decision you can with the information you have.
And just as a friendly warning, trust is like a mirror. When it is shattered, you can glue it back together, but you'll always see the cracks.
So, think long and hard before you go down the road of secret monitoring. Because sometimes, the cure can be worse than the disease.
How to Protect Yourself from Unwanted Keylogging
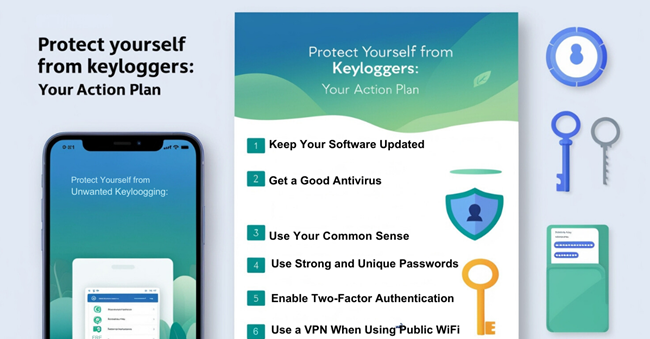
It's time to put on our digital armor and talk about protecting ourselves from unwanted keylogging.
Because in this day and age of always being connected, a little paranoia should do wonders in protecting our virtual persona.
There was a time when I was about as security-conscious as a golden retriever at a frisbee convention. But after a close call with a nasty keylogger (a long story, involving a sketchy free software download and a very embarrassing email to my boss), I wizened up pretty quickly.
So how do you know if your device has been keylogged?
Well, it's not always easy, but there are some signs to watch out for.
If your computer is running slower than a snail in molasses, if you're seeing strange files or programs you don't recognize, or if your antivirus software is suddenly disabled.
These could all be red flags.
Once, I assisted a friend who feared her ex might have installed a keylogger on her laptop. We observed some strange behavior: her cursor jumped across the screen of its own volition, and she received weird pop-ups and advertisements.
After some investigation, we pinpointed the issue. It was a sneaky little keylogger disguised as a system file.
In spite of trying to be stoic, she was, visibly, not happy.
But do not panic!
There are enough measures that can be taken to save oneself from such prying eyes.
Keep Your Software Updated
First and foremost, always update your software.
I know that those constant update notifications are about as welcome as a mosquito at a nudist colony. But I am telling you that they are needed and important.
Often, with software updates come other new versions, and security patches that can protect you from the latest threats.
Get a Good Antivirus
Further down the list, get yourself a good antivirus program.
I do not mean the free anti-virus that came with your PC. Buy a good antivirus program that is comprehensive and also comes with various features over just basic anti-virus.
Like a bodyguard of your digital world, it targets consumer threats to your computer and allows no one who is not worth it to invade your privacy.
Use Your Common Sense
Technology alone can't be enough.
As a general rule, people's heads are the fondest weapons against any malicious application, be it a keylogger or anything else.
Avoid installing programs from unknown creators, do not click any strange buttons, and do not open documents from people you do not know.
Well, there has been this instance when I was close to becoming a victim of a phishing attempt that would have placed a keystroke logging application on my device.
The email appeared real, making it seem as though my bank sent it, but something was wrong. The moment I rolled my cursor over the link, I saw a funny URL.
Such a disaster was avoided!
It is always better to go directly to any site by typing its address than to follow the links given in the emails.
Use Strong and Unique Passwords
Let's move on to passwords.
I know this is boring, you have heard this a million times over, but this needs to be said: each one of your accounts should have a strong password different from the others.
And for the sake of everything decent, do not set your password as “password123” or your date of birth.
Some time back, I assisted a co-worker in retrieving her social media account that had been hacked, can you believe what her password was?
“ILoveCats1985“.
A moment of facepalm right there.
But we know how difficult it is to memorize a million intricate passwords. It is like solving a Rubik's cube while blindfolded.
That's why we need to have a password manager. It is more like a digital safe deposit, in which only a single “master” password is to be kept in mind.
I know it sounds like a sci-fi thing but it works.
Enable Two-Factor Authentication (2FA)
Here's another useful tip: Enable two-factor authentication (2FA) wherever possible.
It's like you are adding an extra deadbolt lock on your digital door. If ever someone is able to take your password away, they still have to get through either your phone or your email to get in.
I've had my fair share of “Ugh, do I really need to enter this code?” moments, but it's saved my bacon more than once.
Use a VPN When Using Public WIFI
Now let's examine the case of public WiFi networks.
It is user-friendly and convenient, definitely, but it offers about as much security as a piece of cardboard with a lock on it.
If you absolutely must use a public Wi-Fi connection, then for the love of all things digital, do use a VPN. It's like an invisible shield that keeps out unwanted internet traffic.
I say this from experience, having had to explain to my credit card company about an awkward situation that resulted after a “free Wi-Fi” offer in an airport.

What to Do If You Suspect That a Keylogger Is on Your Device
Nevertheless, in case you assume that there's a keylogger on your device despite the foolproof precautions you've taken, what is the best course of action?
Do not rush to press the ‘panic' button.
Disconnect from the Internet
First of all, cut off the network connection so that no further transmissions can be made.
Run a Full Scan with Your Antivirus Software
After that, do a complete scan of the whole system employing your antiviral program. If that doesn't catch anything, you might want to consider using specialized anti-keylogger software.
If All Fails, Do a Factory Reset
In very rare circumstances, you may have no other option but to perform a factory reset on your device and basically set it up from scratch.
I know it's annoying.
It's like moving out of one house to another – moving comes with no enjoyment, but when the need arises, one has to do it to move forward.
Just make sure you back up your important files first!
Last but not least, I cannot put enough emphasis on this, educate yourself and others about digital privacy.
Knowledge is power, folks.
The more knowledge you have about the dangers and how to protect yourself, the better you will keep out of trouble.
I have to make it a point to have periodic “digital safety chats” with my family and friends – even if the topics can be rather boring.
Of course, they sometimes roll their eyes whenever I commence my “Internet Safety Ted Talk” but well, rather safe than sorry, right?
Note that protecting yourself in the virtual world is not a one-off event. It is rather continuous in everyone's daily life, such as brushing one's teeth or even pretending to be interested in your colleague's holiday stories.
Get in the habit of regularly performing a security self-audit and learning about new dangers.

Final Thoughts
To summarize, although tracking applications, keyloggers, and other nasty applications may appear daunting, you're not powerless against them.
By keeping your guard up, employing appropriate measures, using the right tools, and good device etiquette, you can keep your online life private and secure.
It may appear very tedious, but believe me, it is a whole lot easier than cleaning up after the event of a security breach.
Well, go on, my cyberwarriors!
Log onto the internet, make calls, and make sure you have lots of fun sending those kitty cat pictures.
Only be careful, alright?
Because any precaution is a good precaution in this era. Be careful out there, and may your passwords be complex, and may the Wi-Fi be secure.
Now, if you have made it this far, congratulations!
You are now officially more aware of what keyloggers are and the dangers that come with their usage than 90% of the population that uses the internet.
Great, give yourself a pat on the back, enjoy a cookie, and venture out to preach the digital security message to all the hitherto digitally indifferent masses.
Future you (not to mention your un-hacked fb) will love you for this.
FAQs
What exactly is a keylogger and how does it work with social media?
A keylogger is a sneaky tool that records what you type. For social media, it can capture your posts, messages, and even passwords. It's like having someone peek over your shoulder while you're online.
Is it legal to use a keylogger on my kid's social media?
It's complicated.
In many places, it's okay for parents to monitor their kids' devices. But it's best to talk with your kids first and check local laws.
Remember, trust is super important in families!
How can I tell if someone's using a keylogger on my social media accounts?
Watch for weird stuff like your computer running slow, strange pop-ups, or your accounts acting funny.
If you're worried, run a good antivirus scan and change your passwords on a different device.
Are there any good reasons to use a keylogger for social media?
Sometimes keyloggers can help protect kids online or recover lost info. But there are often better, more honest ways to stay safe on social media, like open talks and using privacy settings.
How can I protect my social media from keyloggers?
Use strong, unique passwords and two-factor authentication. Keep your software updated, be careful what you download, and use good antivirus software.
And remember, be smart about what you share online!


